My first keysigning party
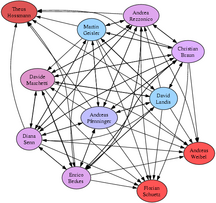 I was to my first keysigning party today, arranged by Diana Senn
in the System Security course at [ETH][]. The results so far can
be seen in the graph on the right, click for a full-sized image.
I was to my first keysigning party today, arranged by Diana Senn
in the System Security course at [ETH][]. The results so far can
be seen in the graph on the right, click for a full-sized image.
The keysigning itself was quite amusing. First we each got a list with the fingerprints of all the keys involved. The list was checked by having each of us read aloud the fingerprint we had brought along. For a random guy it must have been a strange thing to witness: ten geeks each reading their string of forty hexadecimal digits aloud one after another… :-)
The fun continued with the identity check. We lined up in a row and the first guy went past us and checked our IDs along the way. That was it — everybody had proper ID and everything matched.
Coming home I signed peoples keys — if a key had multiple User IDs, then I signed each ID separately. I then sent the signatures on each User ID to the corresponding email address in encrypted mails. This ensures that my signatures wont end up on User IDs which the owner of the private key doesn’t control.
The problem is that anybody can make a user ID with, say, “Martin Geisler — mgeisler@mgeisler.net” as the user information. But if they don’t control that address, then they wont get the signatures sent to it. And if the recipient doesn’t control the secret key, then the encrypted signature is useless to him. So this step binds the email addresses to the key, and should be done if one feels paranoid — or if one want to try and be a crypto-nerd :-)
 In an attempt to make money out of my website, I’ve added advertisements from Google. Now go click on them and make me rich! Bwuhahahaaa! :-)
In an attempt to make money out of my website, I’ve added advertisements from Google. Now go click on them and make me rich! Bwuhahahaaa! :-) I’ve been doing much too much lately, but better late than never:
here’s a report from my visit at the
I’ve been doing much too much lately, but better late than never:
here’s a report from my visit at the  I also got to meet a talking robot there — I saw it coming towards
me so I took at picture of it.
I also got to meet a talking robot there — I saw it coming towards
me so I took at picture of it.